Install essential packages and updates
Login to Kali as root/toor
apt-get update
apt-get install kali-linux-sdr
apt-get install cmake libusb-1.0-0-dev make gcc g++ libbluetooth-dev pkg-config libpcap-dev python-numpy python-pyside python-qt4 libgtk2.0-dev libusb-dev bluez
Install the Bluetooth baseband decoding library
wget https://github.com/greatscottgadgets/libbtbb/archive/2015-10-R1.tar.gz -O libbtbb-2015-10-R1.tar.gz
tar xf libbtbb-2015-10-R1.tar.gz
cd libbtbb-2015-10-R1
mkdir build
cd build
cmake ..
make
make install
ldconfig
Install Ubertooth tools
wget https://github.com/greatscottgadgets/ubertooth/releases/download/2015-10-R1/ubertooth-2015-10-R1.tar.xz -O ubertooth-2015-10-R1.tar.xz
tar xf ubertooth-2015-10-R1.tar.xz
cd ubertooth-2015-10-R1/host
mkdir build
cd build
cmake ..
make
make install
ldconfig
Visualizing the 2.4 GHz spectrum
git clone https://www.kismetwireless.net/spectools.git
cd spectools
./configure
make
make install
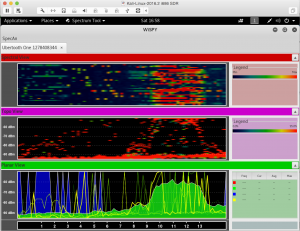
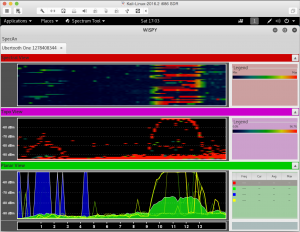
spectool_gtk
The last command will open up WiSPY, click on the “Open Device”, select “Ubertooth One USB”, click on Enable, if you don’t see anything anything on the three Views (Spectral, Topo, Planar) try physically disconnecting and reconnecting Ubertooth-One.
Determine the installed firmware version
#ubertooth-util -V
ubertooth 2015-10-R1 (dominicgs@hydrogen) Mon Oct 12 22:30:57 BST 2015
Known Limitations
The BLE sniffer can only scan 1 Advertisement Channel at a time, out of the 3 (channel 37 on 2402 MHz, channel 38 on 2426 MHz and channel 39 on 2480 MHz). This is a hardware limitation since the Ubertooth has only one narrowband radio chip (the CC2400) and can only tune to a single frequency at a time. So when sniffing the BLE Advertisement channels you have 33.3% chances being on the correct channel for a specific connection. The solution to this issue is to keep trying until you get lucky enough to be on the right channel at the right time, or get 3 Ubertooth dongles each one tuned to monitoring 1 of the Advertisement Channels.
Sniff Bluetooth LE Packets
1. Using the default linux Bluetooth utilities: # /etc/init.d/bluetooth restart && hcitool dev && hcitool scan
2. Using the ubertooth-scan from Ubertooth utilities: # ubertooth-scan -b hcil -t 40 -x
3. Using the ubertooth-btle from Ubertooth utilities (capture Bluetooth LE (Low Energy)) in promiscuous mode:
# ubertooth-btle -p
Sample output:
systime=1481409606 freq=2440 addr=f605c0cd delta_t=24.492 ms
61 bc ed 3c 9e 14 c7 f9 17 3e 44 7d 83 8f 9d 38 2f f8 e5 7d 68 13 a5 42 db ce 67 54 c6 7b c9 d2 67 df 98 40 d1 e4 02 db 18 4c 52 6f c8 0d
Data / AA f605c0cd (valid) / 28 bytes
Channel Index: 17
LLID: 1 / LL Data PDU / empty or L2CAP continuation
NESN: 0 SN: 0 MD: 0
Data: ed 3c 9e 14 c7 f9 17 3e 44 7d 83 8f 9d 38 2f f8 e5 7d 68 13 a5 42 db ce 67 54 c6 7b
CRC: c9 d2 67
4. Using the ubertooth-btle again, but this time save the traffic in a PCAP file for post-examination:
# ubertooth-btle -p -c /tmp/capture.pcap
5. Using the ubertooth-btle again, observe in realtime (you have 1 in 3 chances of being on the correct advertising channel, due to the Known Limitation described earlier):
# mkfifo /tmp/fifopipe0
# ubertooth-btle -f -c /tmp/fifopipe0 &
Open Wireshark | click Capture | Options | click “Manage Interfaces” button on the right side of the window | click the “New” button | in the “Pipe” text box, type “/tmp/fifopipe0” | click Save | click Close | click “Start”
or, launch Wireshark from command line as:
# wireshark -k -i /tmp/fifopipe0 &
6. In case you have 3 Ubertooth devices you can overcome the limitation, described in “Known Limitation” section and monitor all 3 Advertisement channels:
# mkfifo /tmp/fifopipe0 && mkfifo /tmp/fifopipe1 && mkfifo /tmp/fifopipe2
# ubertooth-btle -U0 -A37 -f -c /tmp/fifopipe0 &
# ubertooth-btle -U1 -A38 -f -c /tmp/fifopipe1 &
# ubertooth-btle -U2 -A39 -f -c /tmp/fifopipe2 &
then, either launch Wireshark from command line as:
# wireshark -k -i /tmp/fifopipe0 -i /tmp/fifopipe1 -i /tmp/fifopipe2 &
or,
Open Wireshark | click Capture | Options | click “Manage Interfaces” button on the right side of the window | click the “New” button | in the “Pipe” text box, type “/tmp/fifopipe0”, repeat for “/tmp/fifopipe1” and “/tmp/fifopipe2” | click Save | click Close | click “Start”
Viewing Bluetooth Packets in Wireshark
# wireshark /tmp/capture.pcap
go to Edit | Preferences | Protocols | select DTL_USER and click on Edit… | click on “+” to add | Ensure the new value reads “User 0 (DLT=147)” | in the “Payload protocol” column enter “btle”| OK | OK
Useful Wireshark filters
1. Connection requests and non-zero data packets:
btle.data_header.length > 0 || btle.advertising_header.pdu_type == 0x05
2. Ignore empty PDU (Keep-alive packet):
not btle.data_header.llid==0001