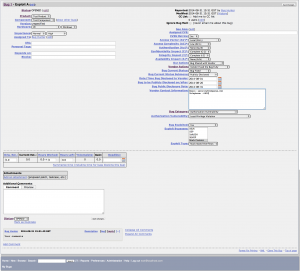
Having discovered bugs in software for which you need to track you actions towards the responsible disclosure, non-disclosure, sale for profit etc can be a headache while dealing with the developers, or the affected companies. We needed a bug tracking management system tailored for exploits and bug hunters, for those who discover the issues, rather than those who fixes them; we had a look around but we could find any… so we took the existing well known bugzilla and modified its database to fit our needs. After one day playing around the first version of exploitzilla born 🙂 get the database file from our github at https://github.com/secuid0/exploitzilla and follow the below instructions to replace bugzilla’s default database with our custom one.
Follow the below sample installation instructions, tested on Debian 3.2.60 with Bugzilla version 4.4.5 (release date 24/Jul/2014):
root@bugzilla:/# wget --ignore-ssl https://github.com/secuid0/exploitzilla/blob/master/exploitzilla.bugs.db.sql
root@bugzilla:/# apt-get install mysql-server apache2
(optional) root@bugzilla:/var/www/bugzilla# apt-get install phpmyadmin
root@bugzilla:/# mkdir /var/www/bugzilla && cd /var/www/bugzilla
root@bugzilla:/var/www/bugzilla# wget http://ftp.mozilla.org/pub/mozilla.org/webtools/bugzilla-4.5.5.tar.gz
root@bugzilla:/var/www/bugzilla# tar xvf bugzilla-4.5.5.tar.gz --strip-components=1
root@bugzilla:/var/www/bugzilla# sudo chown -R www-data:www-data /var/www/bugzilla
root@bugzilla:/var/www/bugzilla# vi localconfig
locate the parameters and change their values to match the below
$webservergroup = 'www-data';
$db_user = 'bugs';
$db_pass = 'bugs$tr0n9P@ss';
root@bugzilla:/var/www/bugzilla# mysql -u root -p
mysql> GRANT SELECT, INSERT, UPDATE, DELETE, INDEX, ALTER, CREATE, LOCK TABLES, CREATE TEMPORARY TABLES, DROP, REFERENCES ON bugs.* to bugs@localhost IDENTIFIED BY 'bugs$tr0n9P@ss';
mysql> FLUSH PRIVILEGES;
root@bugzilla:/var/www/bugzilla# perl install-module.pl --all
root@bugzilla:/var/www/bugzilla# ./checksetup.pl
....after a while and if all goes well you will be prompted to enter the account details for the new bugzilla administrator...
Enter the e-mail address of the administrator: root@localhost.com
Enter the real name of the administrator: Bug Hunter
Enter a password for the administrator account: password
Please retype the password to verify: password
root@bugzilla:/var/www/bugzilla#mysql -u root -proot bugs < exploitzilla.bugs.db.sql
root@bugzilla:/var/www/bugzilla# vi /etc/apache2/sites-available/default
and add the below after the <VirtualHost *:80>
<Directory /var/www/bugzilla>
AddHandler cgi-script .cgi
Options +ExecCGI
DirectoryIndex index.cgi index.html
AllowOverride Limit FileInfo Indexes Options
</Directory>
root@bugzilla:/var/www/bugzilla# /etc/init.d/apache2 restart
Open your web browser and point to http://ip/bugzilla/ use “root@localhost.com” for username and “password” as password. Do not forget to change the password to a stronger one prior moving to production.
Notes:
- Official bugzilla configuration guide http://www.bugzilla.org/docs/4.4/en/html/configuration.html
- To reset your exploitzilla password, run as root from
/var/www/bugzilla# perl checksetup.pl --reset-password=root@localhost.com - Sample /etc/apache2/sites-available/default file
- Sample /var/www/bugzilla/localconfig file
- Incase you ever need to reset the bug id counter:
ALTER TABLE bugs AUTO_INCREMENT=1;